Trace Vulnerabilities
& Monitor Exposures
Trace and discover when organizations' private repositories are exposed and find vulnerable GitHub usernames for takeover opportunities. Get instant alerts for high-value security vulnerabilities.
Why Security Researchers Choose iTrace.today
Repository Exposure Tracing
Trace and instantly detect when organizations' private repositories are publicly forked and exposed. Find security vulnerabilities before anyone else.
Takeover Vulnerability Tracing
Trace repositories for vulnerable GitHub usernames and potential takeover opportunities. Find broken links that could lead to account hijacking.
Instant Alerts & Integrations
Get notified the moment vulnerabilities are discovered. Integrate with Slack, Discord, or webhooks to never miss a bounty opportunity.
Comprehensive Vulnerability Tracing
Trace both repository exposures and takeover vulnerabilities in one platform. Identify insider threats and policy violations.
How iTrace.today Works
Trace & Monitor
Add organizations to trace for exposed repositories and monitor repositories for takeover vulnerabilities.
Trace Vulnerabilities
Our system continuously traces GitHub for exposed private repositories and monitors for vulnerable usernames.
Report & Earn
Get immediate alerts when vulnerabilities are discovered. Report these security issues for bug bounties.
Powerful Vulnerability Tracing Features
Repository Monitoring
Monitor unlimited organizations for exposed private repositories
Takeover Detection
Find vulnerable GitHub usernames and potential takeover opportunities
Webhook Integrations
Automate your workflow with powerful webhook integrations
Own Your Security Intelligence
Get the complete source code and run iTrace.today on your own infrastructure. No monthly fees, no vendor lock-in, complete control.
Lifetime Access
Pay once, own forever. No recurring fees.
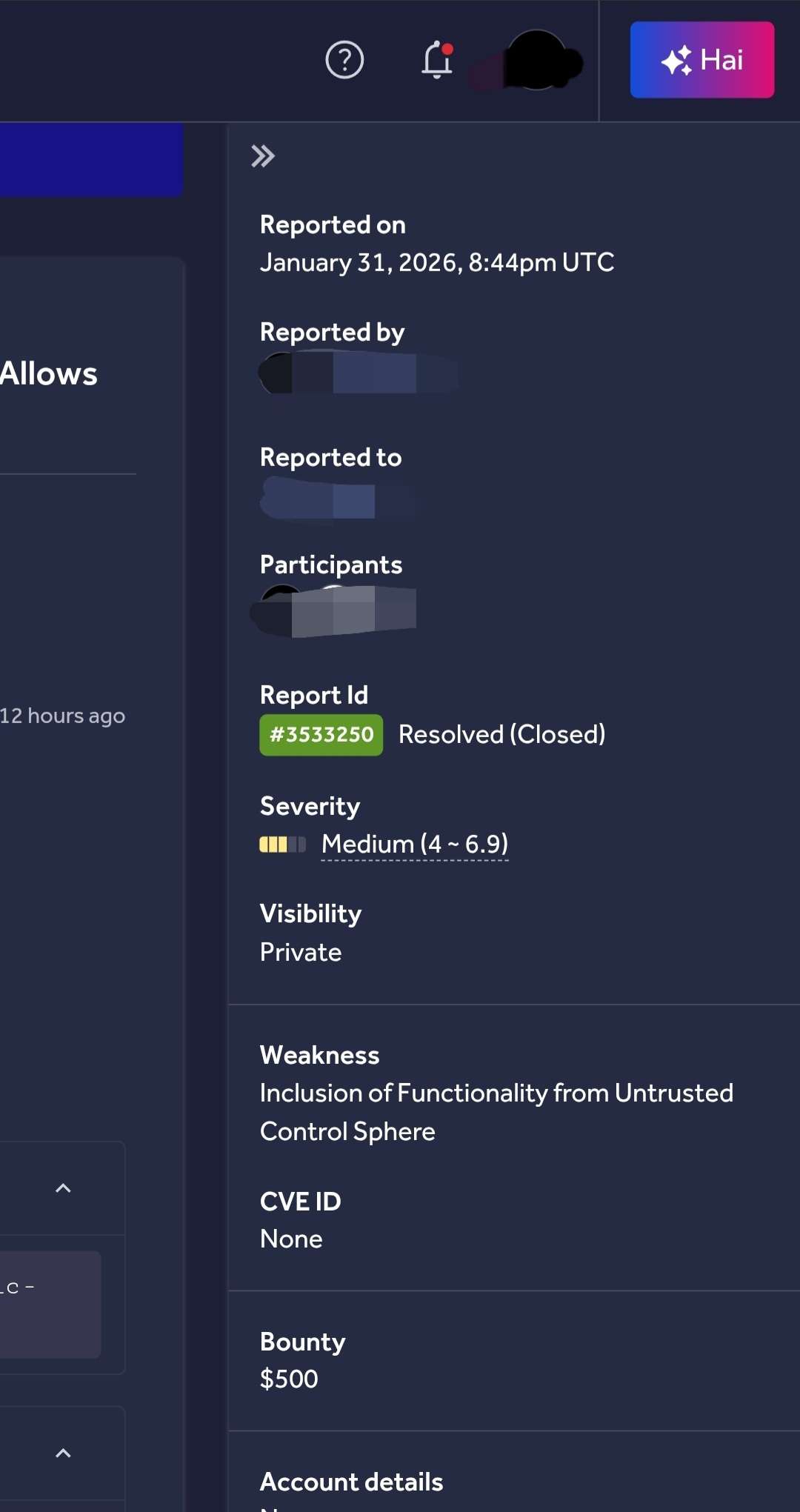
High-Value Discoveries by Our Users
Real bug bounty rewards earned using iTrace.today's advanced vulnerability tracing capabilities
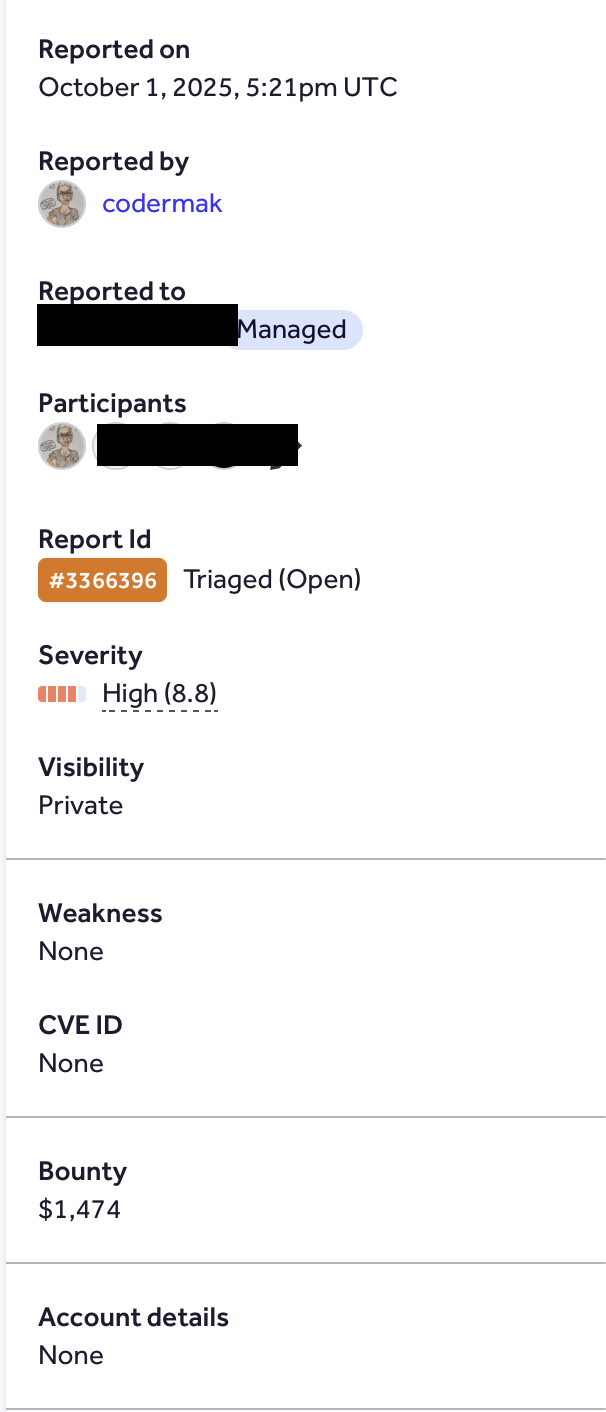
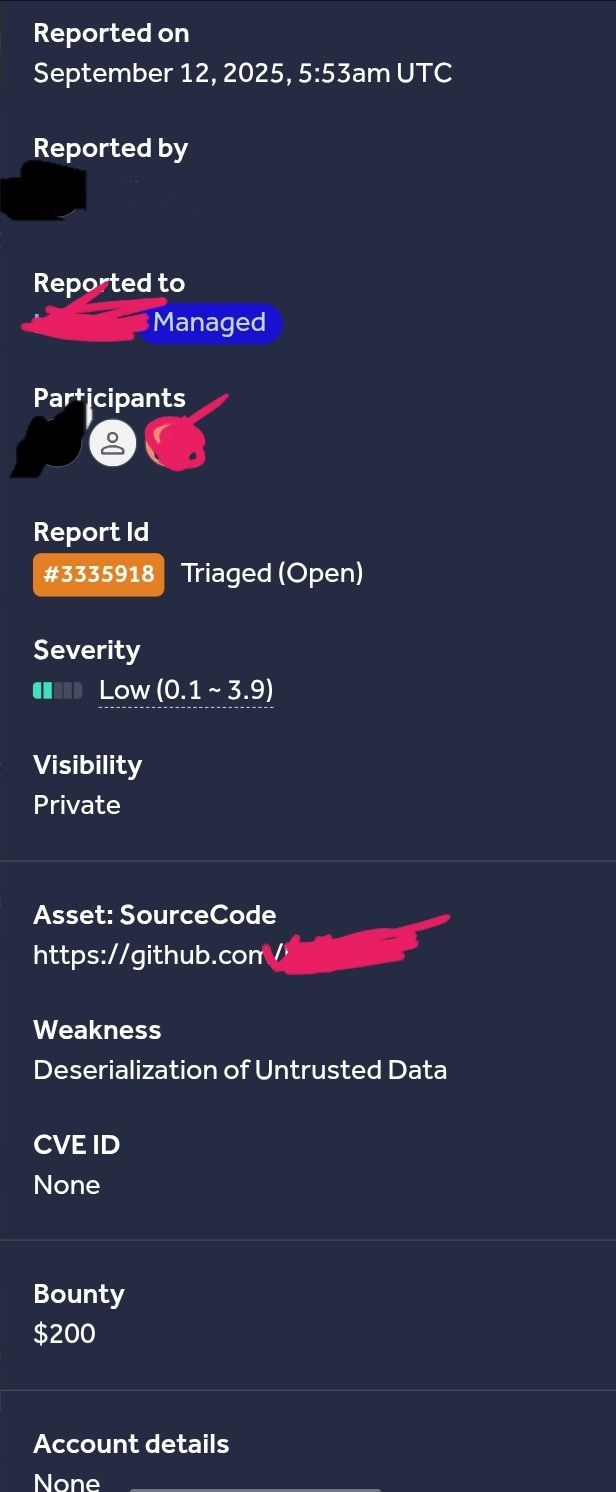

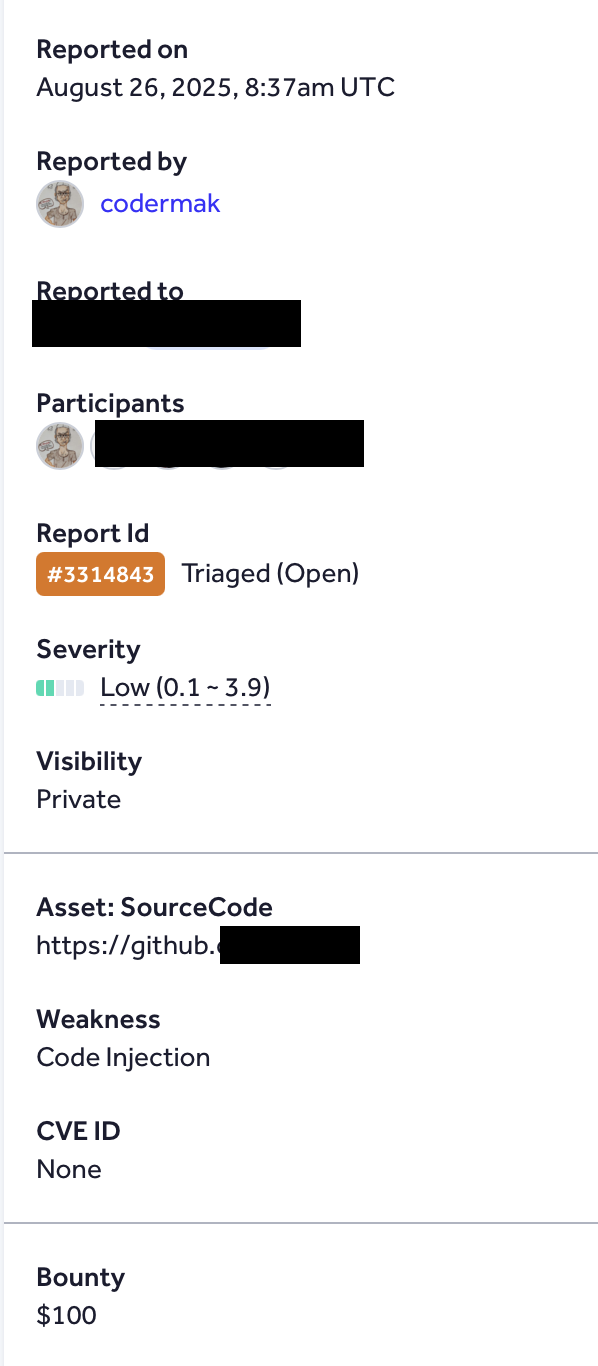
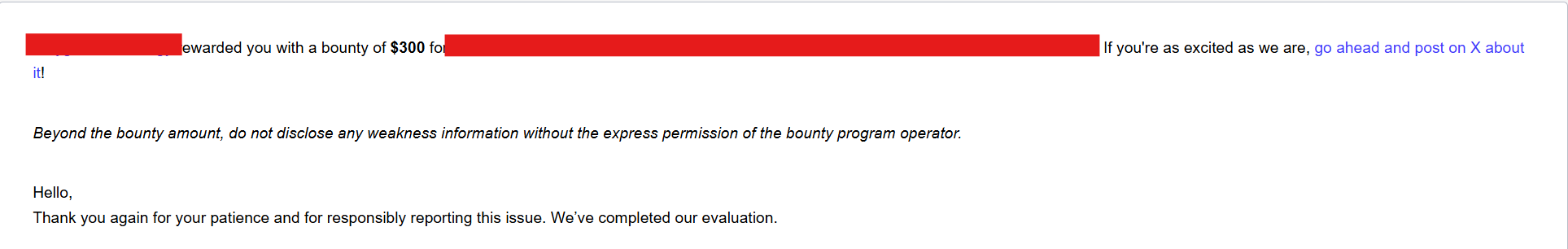




Have a success story to share?
Get Started & Share Your Story